3.4.1.2:STM32H5 Extends
1.Preparatory Work
1.1Software and Hardware
- software: Power Writer 1.4.0.5 [Build:2025-09-02 18:06:05]
- Hardware: PW200 ifVer:1.01.44,PW300 ifVer:1.01.44,PWX1 ifVer:1.00.38.Any one of the devices is supported.
(The above version and subsequent versions all support it. If there are any adjustments, the corresponding updates will be made in the subsequent documents.)
1.2 OBKey and BIN
The OBKey file is generated by the STM32 Trusted Package Creator based on an XML template.
- DA_Config.obk
- STiROT_Config.obk(optional)
- STiROT_Data.obk(optional)
- board_password.bin(STM32H503)
- data_soc_mask.bin(STM32H503)
1.3Certificate and Private Key
Taking the root certificate as an example:
- cert_root.b64
- Key_1_root.pem
1.4Password File
- password.bin
2.Function Entrance
PowerWriter® support for manufacturer-specific features, are using the plug-in mode, you can support the specific features required by any manufacturer, the method of entry and other brands of the support method is consistent, in the selection of the chip, such as in the toolbar on the right side of the most a plug-in support icon appears, the currently selected chip has a plug-in support function, as shown below:

After selecting the STM32H5 family of chips, an Extensions button appears on the right side of the toolbar, defined as Vendor Specific Plug-In Functions, which can be clicked to enter the STM32H5 Security Extensions screen as shown below:
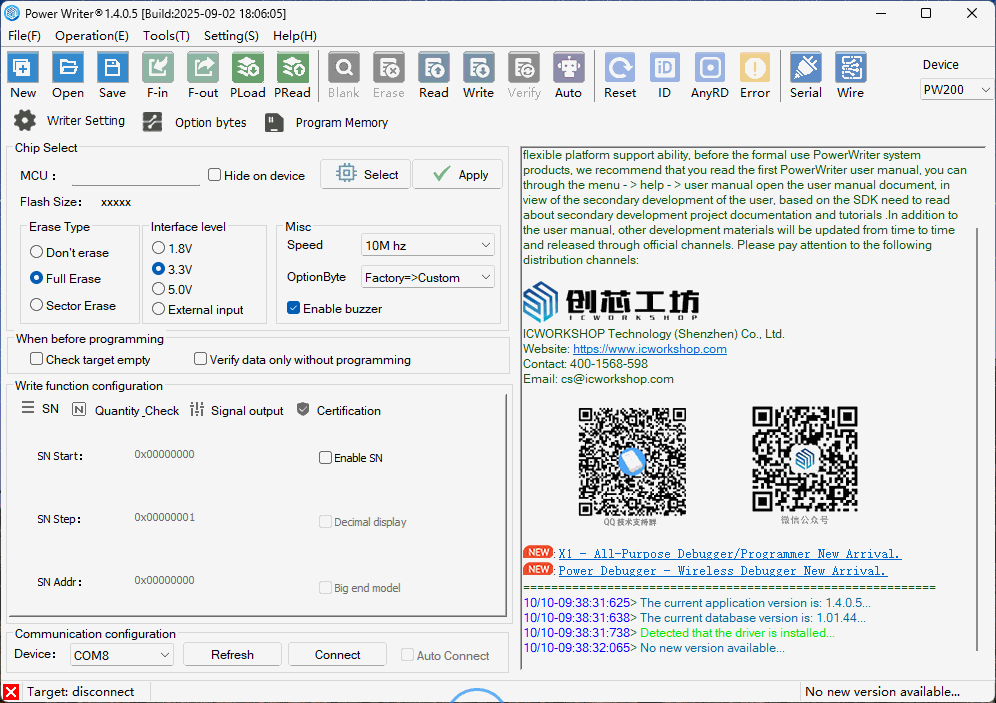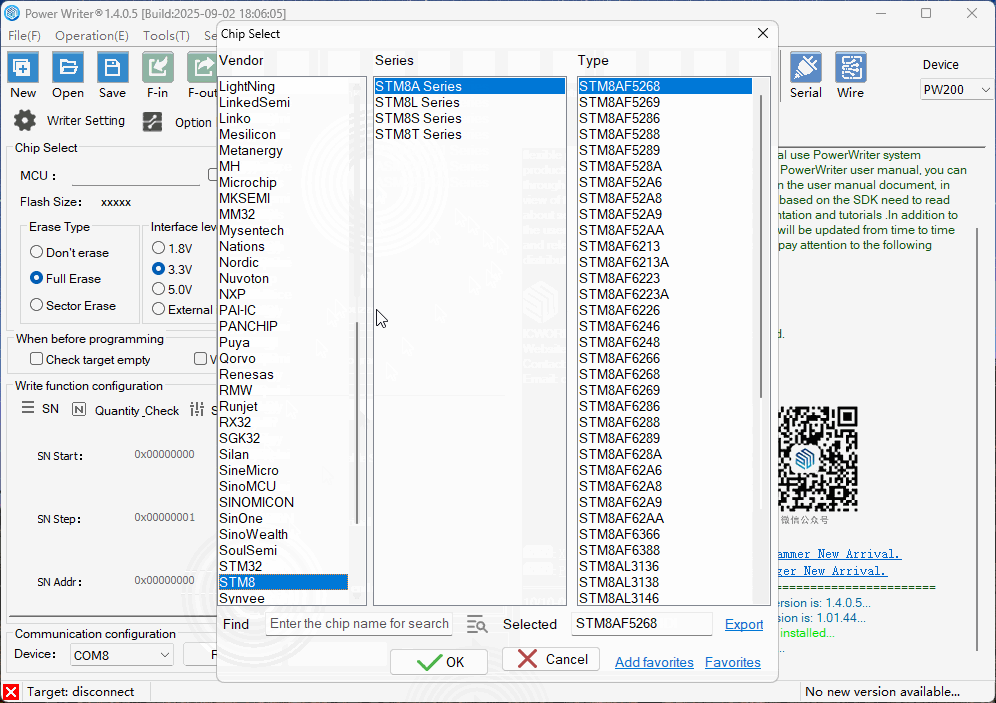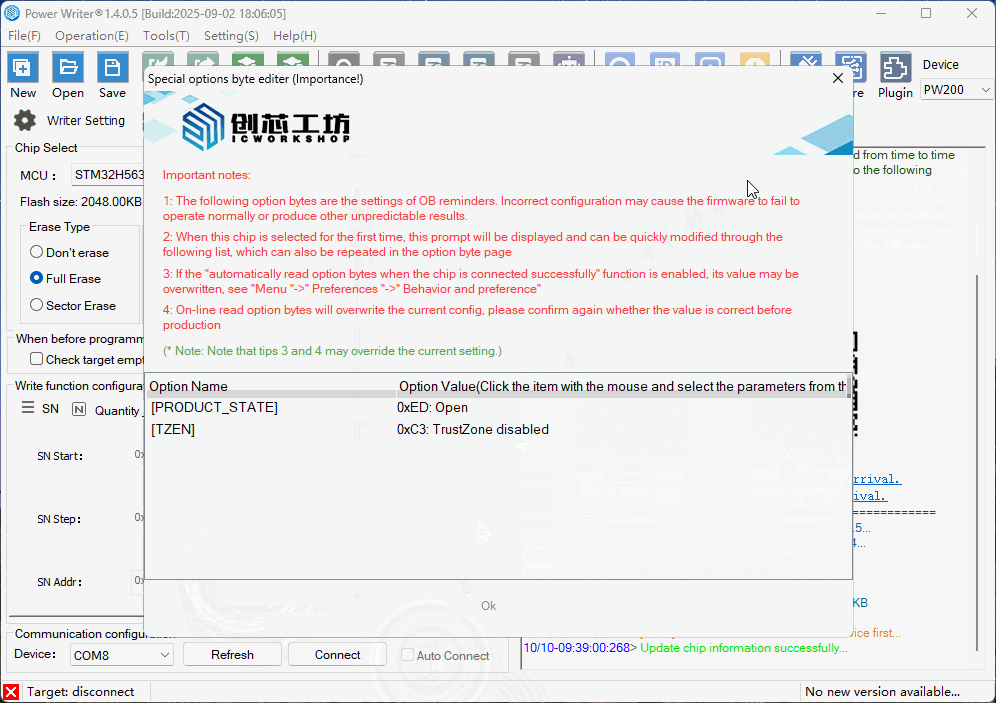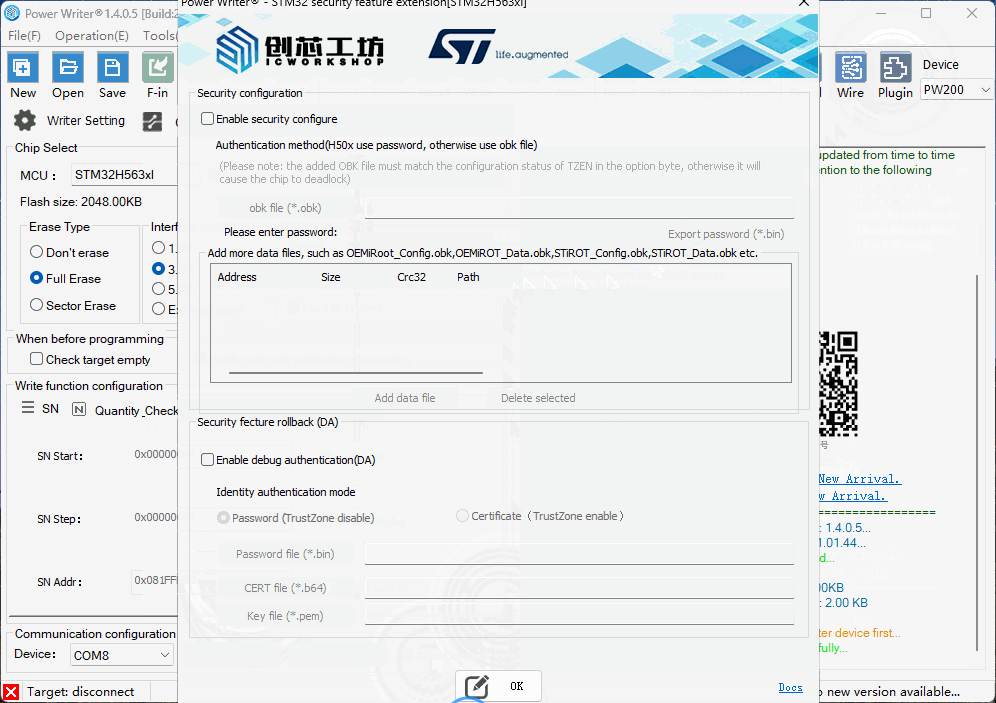
The plugin is divided into two sections: the PROV OBKey file addition area, and the DA password or certificate and private key file addition area.
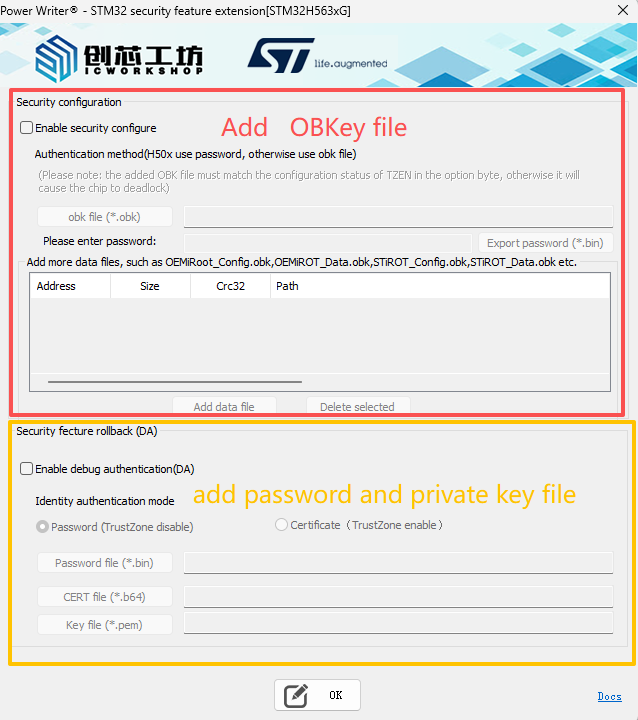
For the STM32H5, setting the product state in online mode is ineffective. In offline mode, if the product state is not "open," a configuration file must be added.
3.Safety Function Configuration
Click "Enable security configure" button, it will start the security configure function, First, add obk files used for debugging and certification, and more data files can be added as needed.
The security configure supports *.OBK file mode (STM32H56/STM32H57) and password mode (STM32H50), the plug-in automatically selects the appropriate mode according to the current chip, for example, selecting the chip for STM32H50 series. The plug-in automatically selects the appropriate mode according to the current chip, such as selecting the STM32H50 series chip. In addition to setting the password, it can export the PASSWORD.bin file for unlocking the chip to be used in the regression.
3.1 STM32H503 File Addition (Optional)
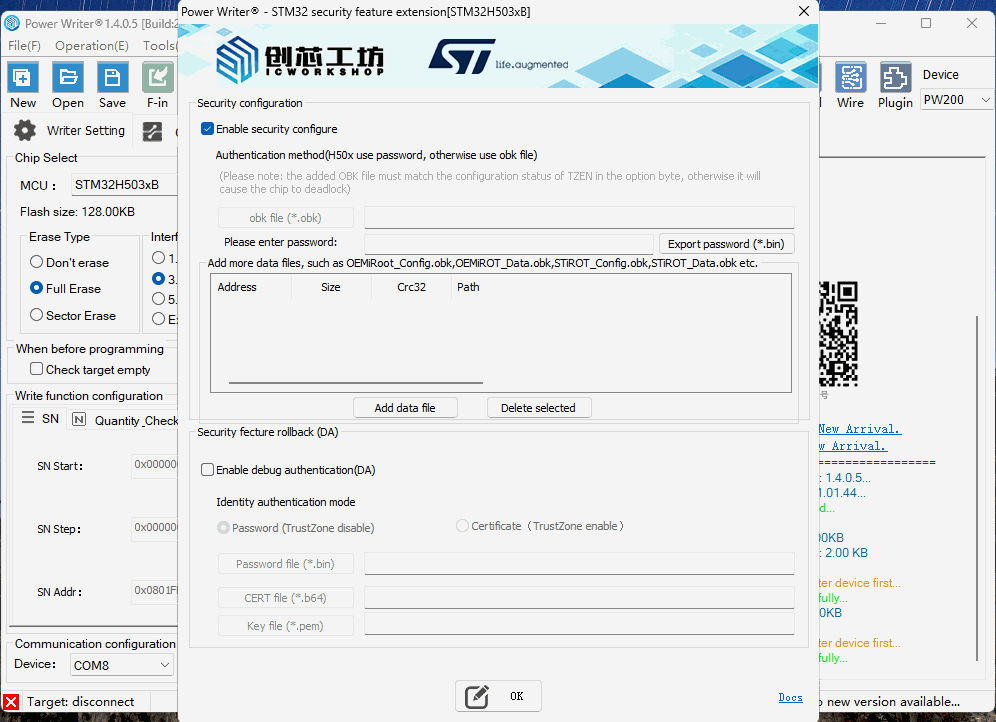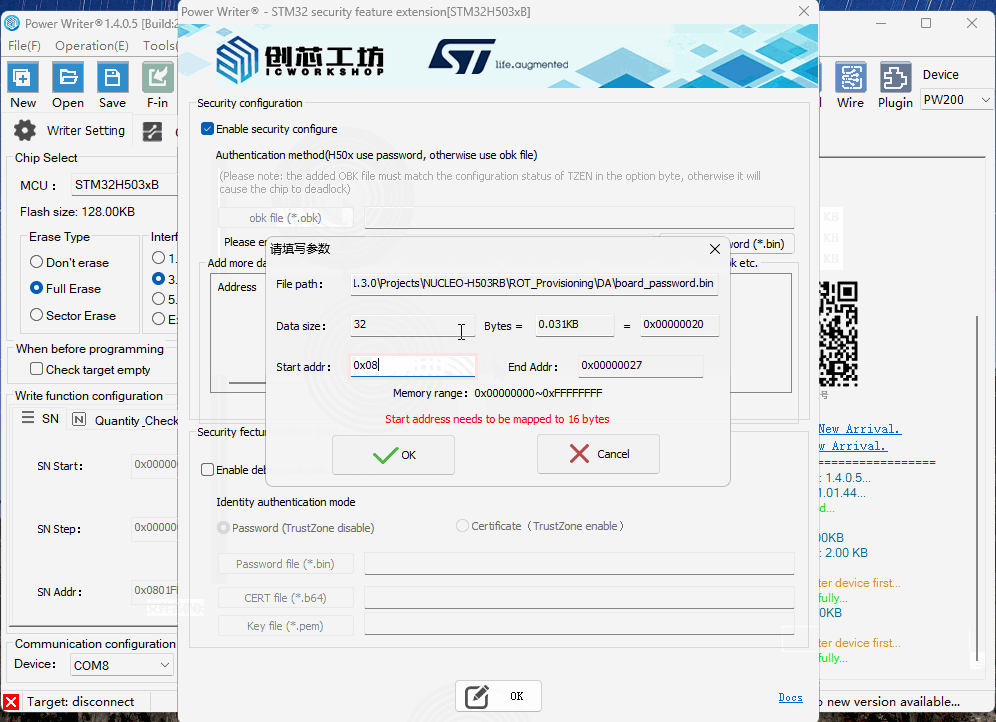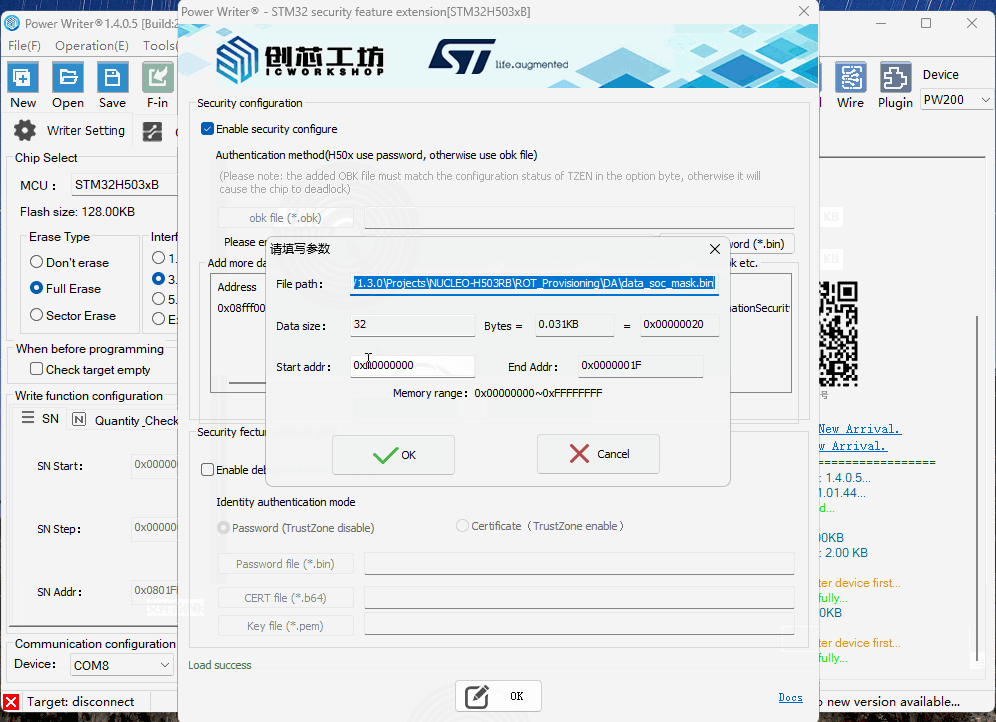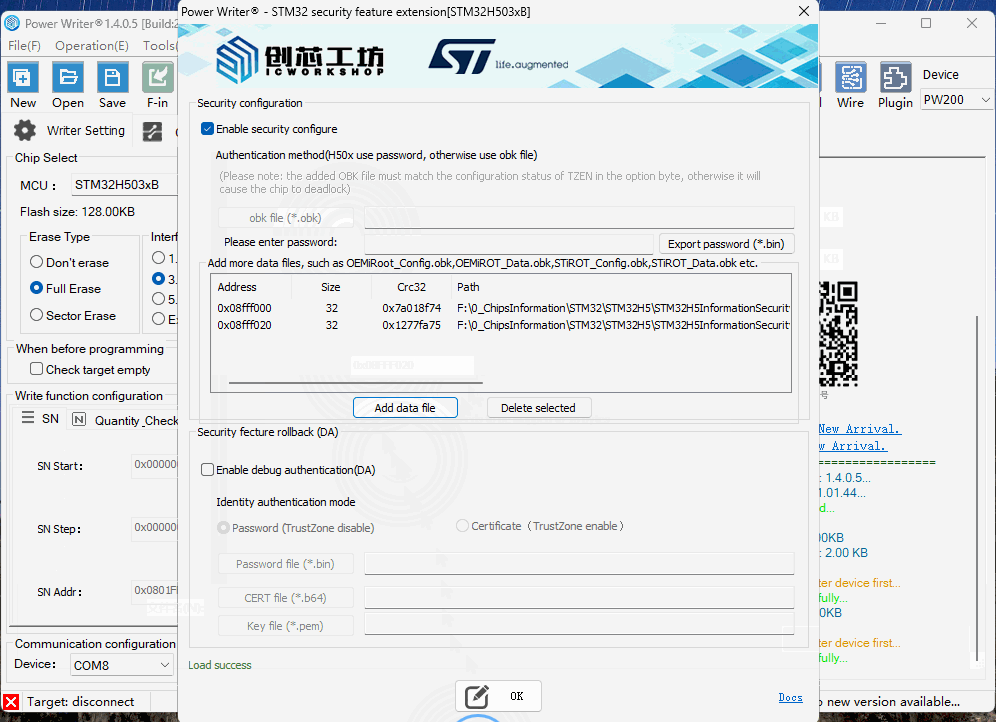
The STM32H503 stores data in OTP (One-Time Programmable) memory. The starting address for STM32H503 OTP is 0x08FF F000, and the address must be entered manually.
After checking 【Enable Configuration Function】, click 【Add Data File】 to select a .bin file, then set the starting address for the data.
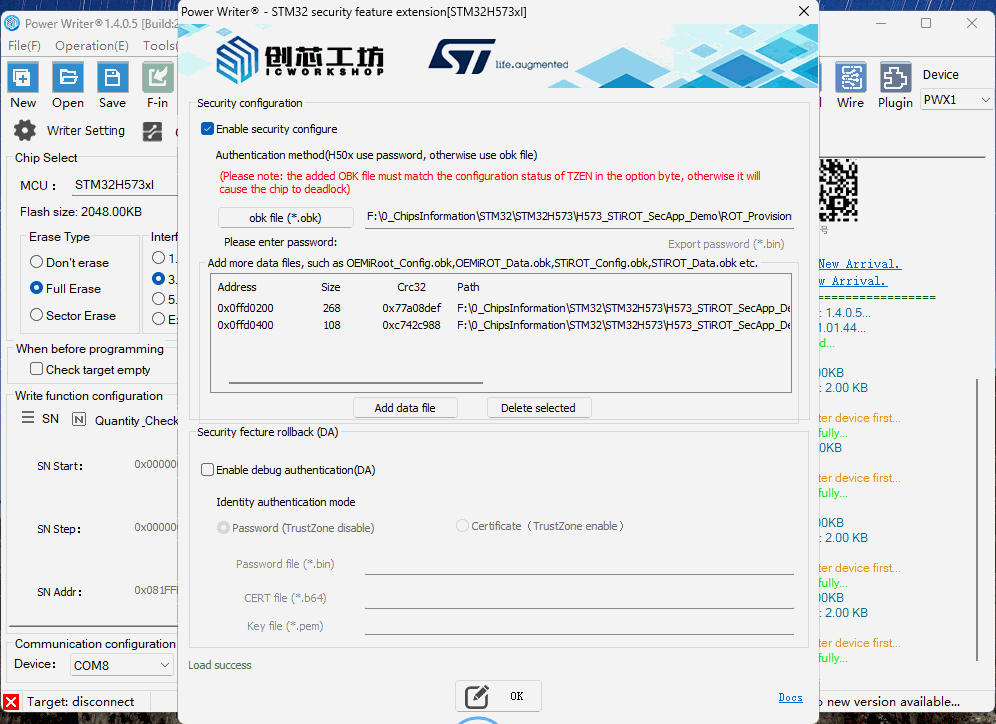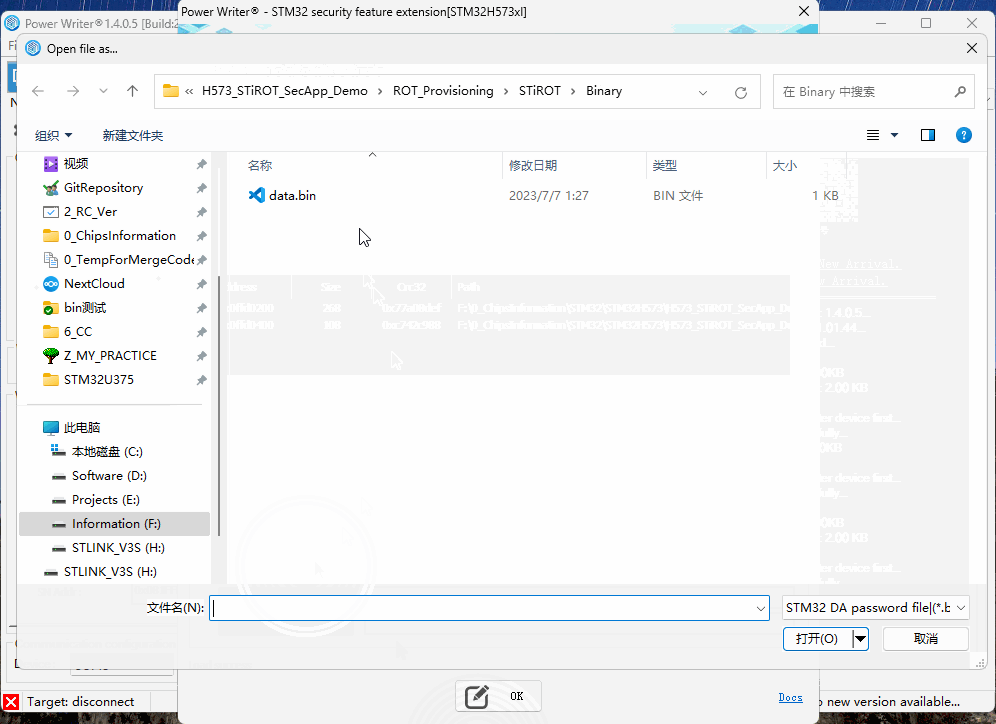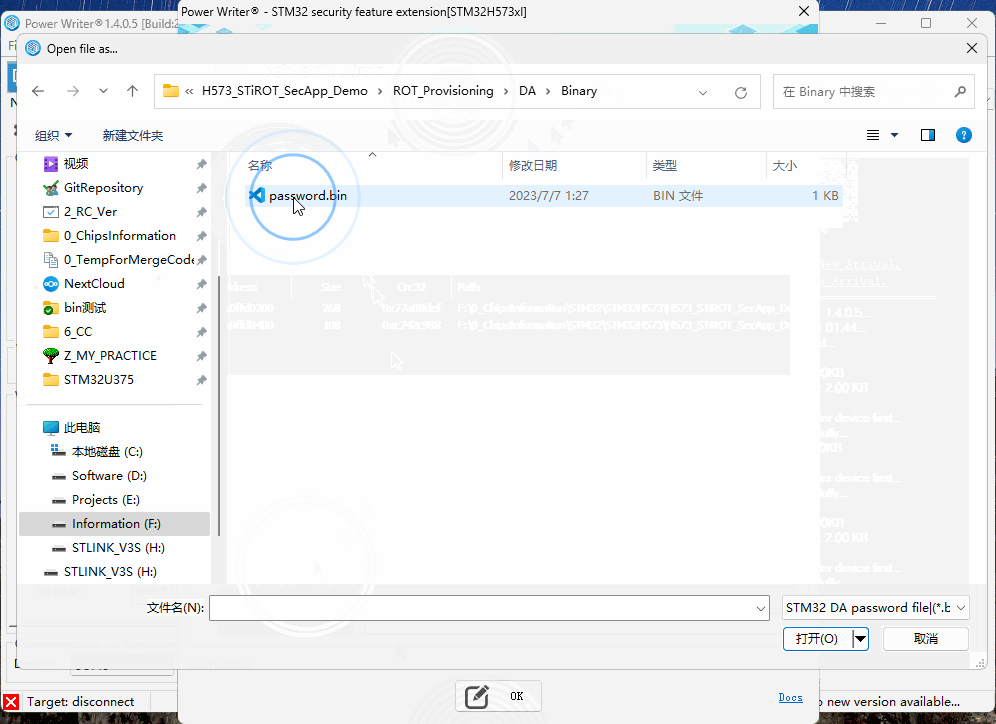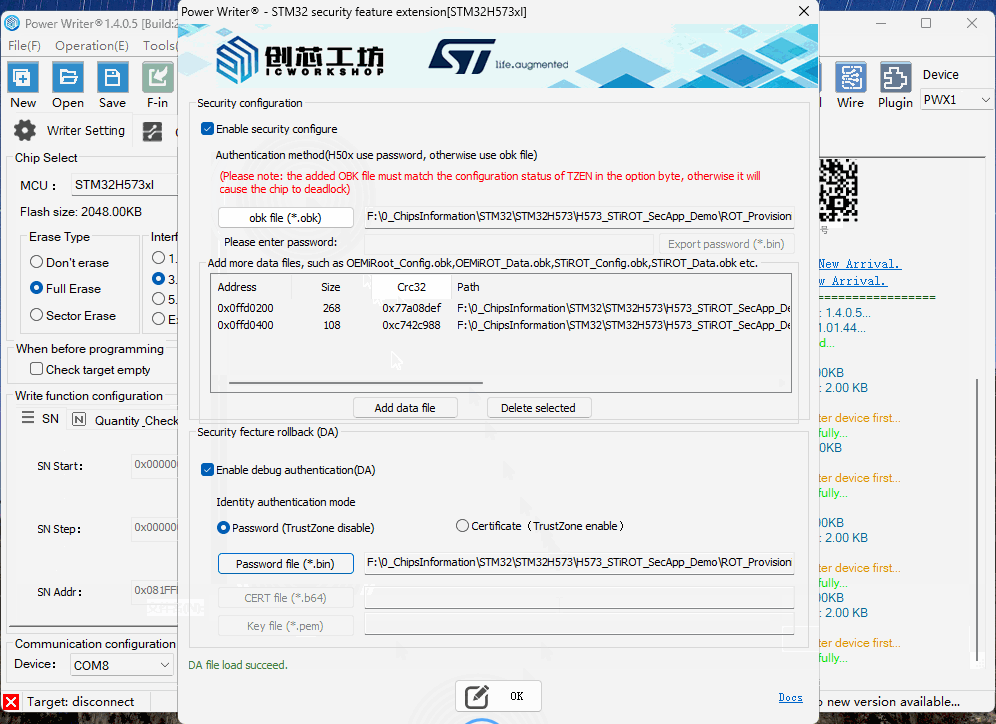
3.2 OBKey File Addition (Optional)
After checking 【Enable Configuration Function】, add the OBKey file.

4.Debug authentication
Click the "Enable Authentication" button to activate the secure feature regression function (performing debug authentication on the chip for analysis or unlocking). Secure feature regression configuration supports two modes:
- *.bin file format (TrustZone disabled)
- Certificate format (TrustZone enabled)
4.1 Regression in Password Mode, Importing bin File (Optional)
After checking 【Enable Authentication】, select 【Certificate (TrustZone Enabled)】, then add the corresponding file.
4.2 Certificate and Private Key File Addition (Optional)
Import a .b64 certificate file and a .pem private key file.
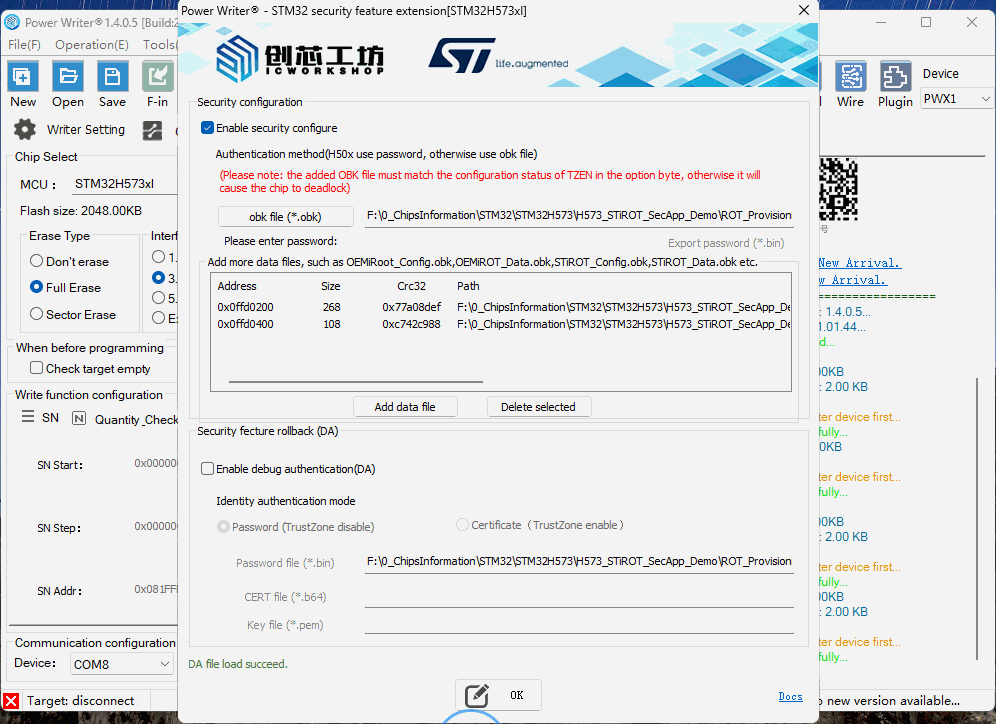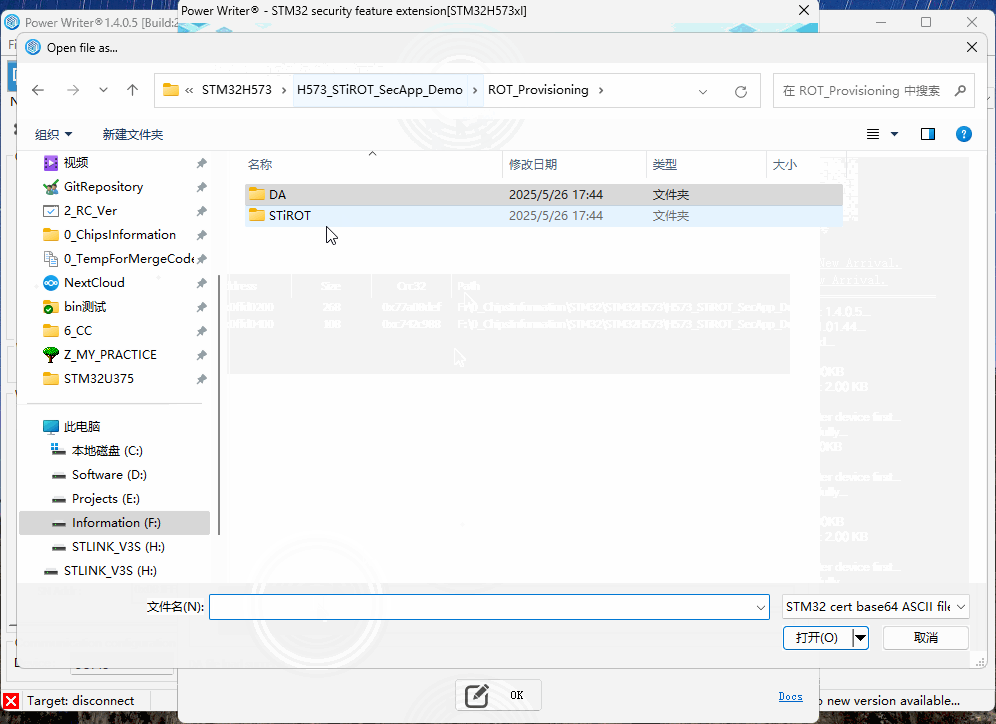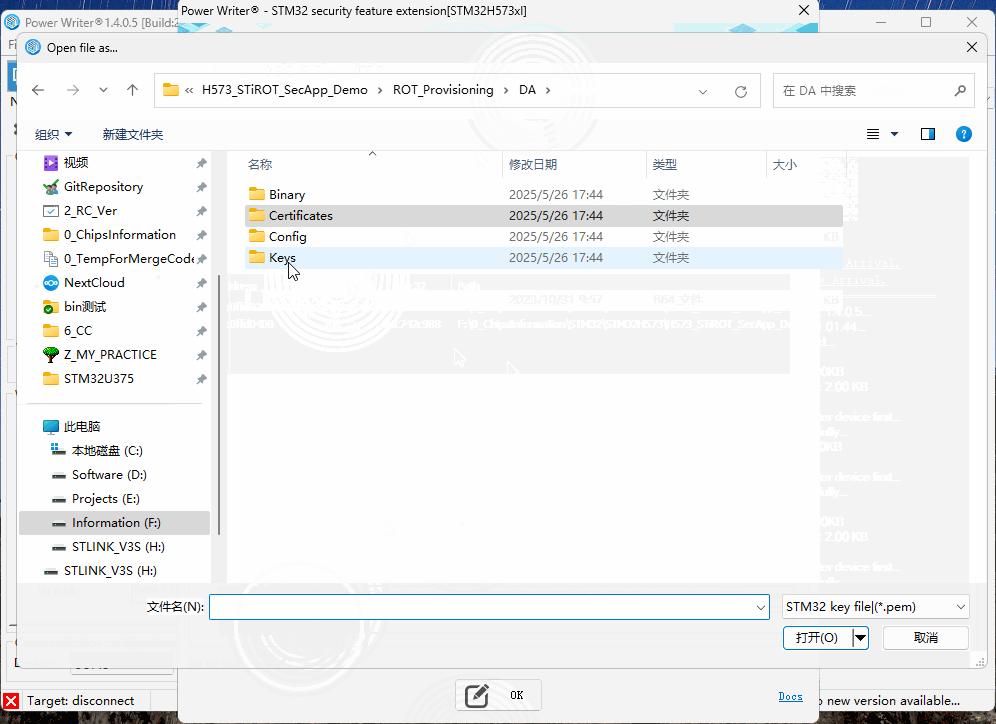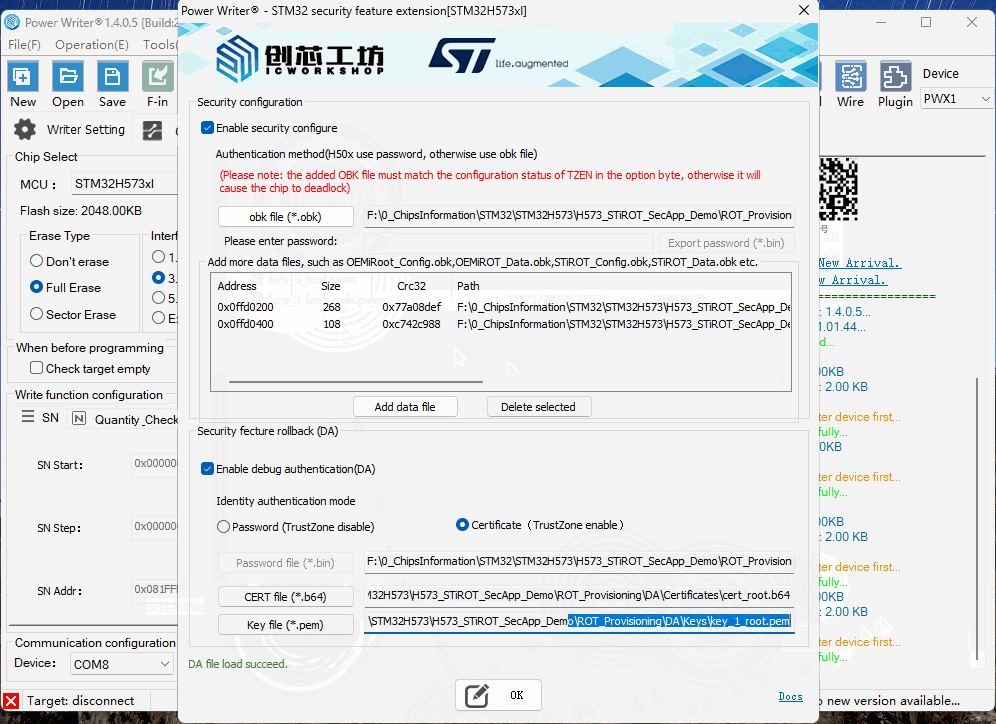
After checking 【Enable Authentication】, select 【Certificate Authentication (TrustZone Enabled)】, then add the respective files.
As of now (2024/02/29) the current security features configuration and return to support the form of password, does not support the form of certificates, the future will be updated to support certificates, if there is an update, please pay attention to the detailed changelog, or consult technical support and customer service.
STM32H50x series Only support password form, STM32H56x, STM32H57x support both password and certificate form (Debugging and authentication (DA) that supports opening trust zone but not certificate mode).
About "Secure Boot"
- If the "OEMiROT" function is enabled, the configuration option bytes in accordance with the specifications of the OEMiROT_Boot.bin file must be followed to avoid program startup failure.
- If the "STiROT function" is enabled, please correctly configure the option bytes to ensure the normal installation and startup of the program.
- Flash Secure Watermark
- SRAM2 ECC
- SRAM2 Reset
- setting :TZEN = 0xB4( enable TrustZone)
- BOOT_UBE = 0xC3(start from ST-iROT)
At present, the extended function only supports offline mode .
The host computer and programmer do not verify whether the TZEN configuration matches the added OBKey file.
Functional dependence
Security function configuration: only when the option byte-byte 1(PRODUCT STATE) is not Open(0xED), the added configuration file (.obk) is written into the OBKey area of the chip.
fallback of security function: When the chip cannot be connected or the option bytes are restored to the default, programming device will use the files added under this function for Full regression.Currently, only full regression is supported.
- When the chip cannot connect normally, the programmer attempts a full rollback. If the user has not enabled the DA function or has not added the correct certificate and private key, an error is returned, resulting in connection failure or DA authentication failure.
- During use, the BOOT pin must be kept pulled down, and the NRST pin must be connected to the programmer's RST pin.
- If the program fails to run after programming, check whether the option byte settings are correct.
Before use, please verify that the file used for rollback matches the configuration file completely, and the loss caused by the user's wrong configuration shall be borne by the user.