4.3 Project Configuration
4.3.1 Configuration
The Device Configuration page, which contains most of the configuration needed for signature setup, see the detailed labeled information as shown below:
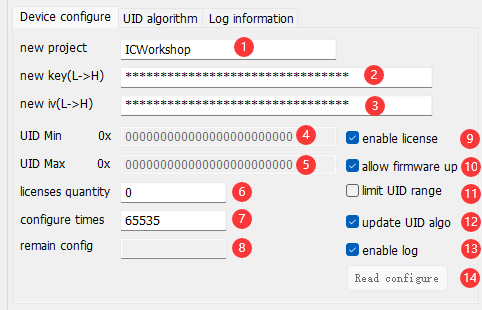
- New project : New project name, this field is copied from the PowerWriter® project.
- New Key:New Password, this field is copied from the PowerWriter® project.
- New IV:New vector, this field is copied from the PowerWriter® project.
- UID Min:Limit UID Min.
- UID Max:Limit UID maximum.
- Licenses quantity: Controls the number of actual authorizations available.
- Configure times: The current number of times the ICWKEY device can change the configuration, the default is 65536, every time you configure, the counter -1, when it is 0, it will no longer be able to make changes!
- Remain config: The number of modifications remaining for the current device.
- Enable Authorization:Switch authorization enable / disable .
- Allow firmware upgrades:Whether to allow firmware upgrades.
- Limit the UID authorization range: Limit the use of UIDs.
- Allows updating the UID algorithm: Whether or not to allow the authorization algorithm to be updated.
- Enable log: Records authorisation log information, often used for reports.
- Read the target configuration: Reads the configuration information of the current device.
- After the new project name, password, and vectors are copied and updated from the PowerWriter® project, please save the project to avoid losing it, or else ICWKEY will not be able to connect.
- UID setting, valid only when Limit UID Authorization Scope is turned on.
- Configurable number of times: Please note that this position is not an authorized number, but the number of times the device can change the settings, when the number of times is 0, the device will be locked, and can not be repeated to modify, unless necessary, do not modify this information.
4.3.2 UID
Currently comes with two signature algorithms, the first is Matrix Signature, a random matrix encryption algorithm, the advantage is that it takes up very little resources, and it can sign and verify the target chip to prevent the firmware from being directly copied and used, and the second is ECDSA Digital Signature, a non-stacked electronic signature algorithm, which is currently a very strong encryption algorithm, and the algorithm is difficult to crack, but it is still necessary to further enhance the protection of the code itself to prevent the signature from being removed. However, it is still necessary to further enhance the protection of the code itself to prevent the signature from being removed, and can be integrated with the MCU Common Advanced Software Protection Library to enhance the security of the firmware, please contact us cs@icworkshop.com。
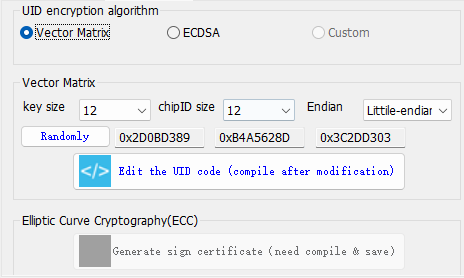
4.3.2.1 Matrix
This setting is generally sufficient to keep the default settings, which can randomly generate Keys.
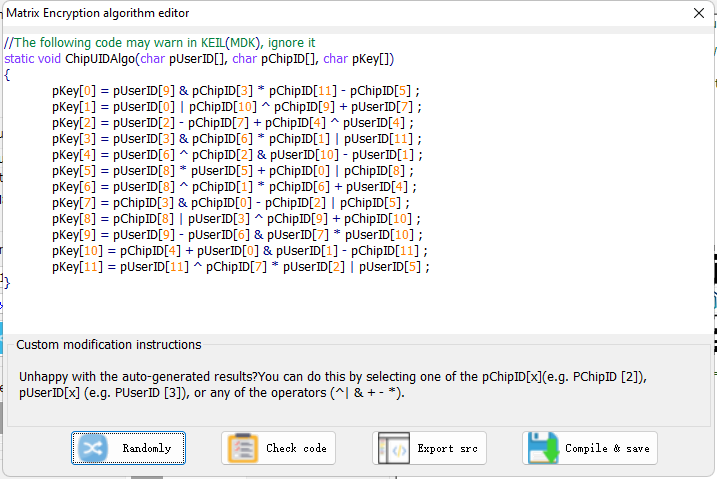
Randomly generate the Matrix information, when the operation is complete, click Export Source (to be integrated into the firmware), and finally click Compile and Save to update the settings.
After setting, please be sure to click the save button to avoid the setting is not updated, if you forget to operate, you can perform the operation again and export the source code.
4.3.2.1 ECDSA
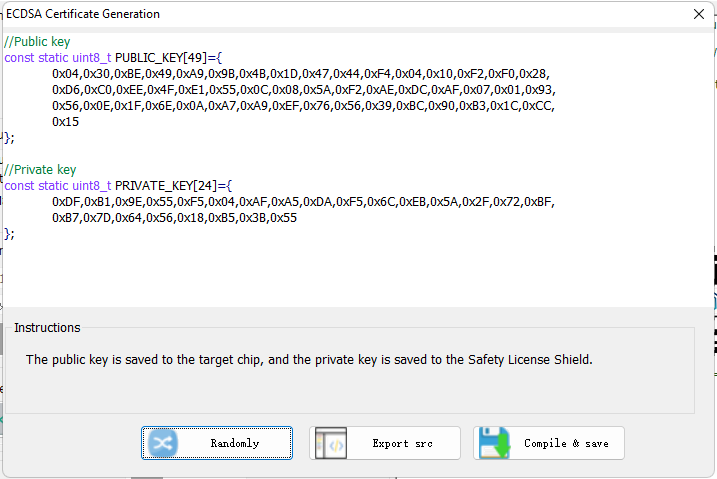
Random Generation: Generates ECDSA digitally signed public-private key pairs.
Export source code: Export source code information for integration.
Compile and Save: After the operation is completed, the settings are saved and updated.
After setting, please be sure to click the save button to avoid the setting is not updated, if you forget to operate, you can perform the operation again and export the source code.
4.3.3 Logger
Total number of authorizations: Total number of authorizations currently configured for the device.
Used: Accumulation of the number of times authorization is currently requested.
Number of successes: Accumulation of the number of times a certificate has been successfully distributed.
Number of failures: Total number of distribution failures.
Unknown Error: Unknown error, generally categorized as the number of failures.
Testing authorization:
Filling in the ID information will generate the authorization information of the current chip, which is commonly used for debugging.
- Please be aware that the signature information returned by ECDSA authorization test may not be the same every time.
- Number of failures + number of successes + unknown errors = number of times used.